As more businesses adopt remote work, managing risks becomes crucial. Organizations must identify unique risks tied to remote teams, including cybersecurity threats and operational challenges.
Recognizing these factors is key to keeping productivity high while protecting sensitive information in a digital space.
Managing a remote workforce means creating strategies to handle the difficulties of overseeing employees who work away from the office.
This involves assessing risks related to technology use, communication practices, and data protection.
A solid plan helps companies avoid potential issues and maintain a secure and productive virtual workplace.
Understanding the Unique Challenges of Managing Remote Teams
Managing remote teams comes with specific challenges that are different from traditional office environments. Important areas include employee management in remote settings and how to monitor performance for distributed teams.
One big challenge is keeping communication effective among team members who are far apart.
Without face-to-face interaction, misunderstandings can happen easily, affecting teamwork and morale. Also, measuring productivity can be tough; managers often find it hard to see employee output when they can’t observe daily activities directly.
Key Issues Faced by Remote Teams
Remote teams face several important issues:
- Communication Security: It’s vital to have secure channels for conversations, especially as cyber threats rise.
- Technology Adoption: Quickly using new tools can confuse employees or lead to inconsistent usage.
- Operational Resilience: Companies need to be flexible enough to change processes quickly during unexpected disruptions.
These challenges show the need for strong training programs that provide employees with essential skills while promoting good digital security practices.
Strategies to Overcome These Challenges
To improve remote team productivity and make operations smoother, organizations should adopt specific strategies:
- Invest in effective communication tools made for virtual collaboration.
- Set clear guidelines on expected results along with regular check-ins.
- Foster an open feedback culture where team members feel safe discussing concerns about their workflow or technology use.
By focusing on these approaches, companies can build an engaged workforce ready to tackle the challenges of remote work environments.

Cybersecurity Risks in the Remote Workplace: A Comprehensive Overview
As businesses shift toward flexible working arrangements, cybersecurity becomes a major concern.
Workers now face more online threats like phishing attacks or malware infections during common tasks such as file sharing or video calls.
Understanding common cybersecurity threats helps businesses prepare and protect their assets from breaches through effective data breach prevention techniques.
Using secure collaboration tools that have encryption features is essential for keeping all communications confidential.
Common Cyber Threats Encountered by Remote Workers
Remote workers often deal with various cyber threats:
- Ransomware Attacks: Malicious software that locks files until a ransom is paid presents serious financial risks.
- Phishing Attempts: Fraudulent emails tricking users into sharing personal info highlight the need for ongoing training.
- Endpoint Protection Gaps: Devices used outside company networks must have stronger defenses against unauthorized access attempts on public Wi-Fi networks often used at home offices today.
Organizations should prioritize educating their staff on spotting signs of such dangers while reinforcing safe browsing habits during their remote work time away from central office facilities!
The Importance of a Robust Cybersecurity Framework
Having a strong cybersecurity framework is key to protecting sensitive company data as threats grow daily! Using methods like a zero-trust security model makes sure every user request gets thorough verification, no matter if it comes from inside or outside established boundaries of the system.
Plus, adding multi-factor authentication (MFA) provides another layer of security for accounts which lowers the chances of successful breaches happening later on—preventing potentially harmful effects on brand reputation and long-term sustainability efforts!
Operational Risks and Their Impact on Remote Teams
As remote work grows, companies face different operational risks that can hurt team productivity.
Managing these risks is key to keeping a motivated workforce.
Key concerns include employee management in remote settings, technology adoption challenges, and the need for solid performance monitoring systems.
Managing Remote Team Productivity and Performance
Keeping remote teams productive relies on effective performance tracking methods designed for virtual work.
Companies should implement specific Key Performance Indicators (KPIs) including:
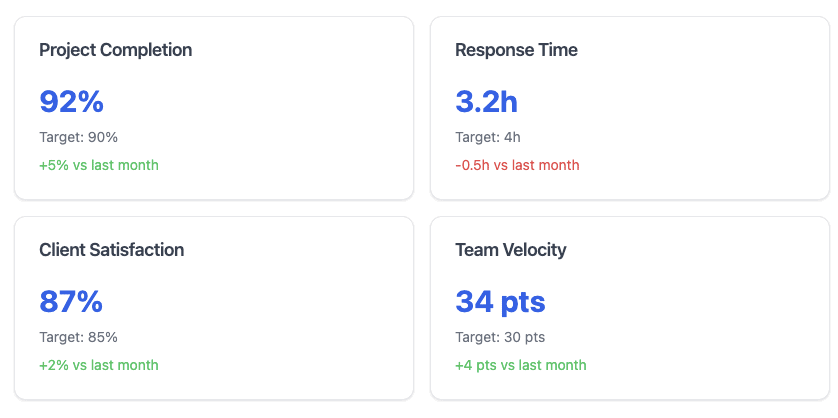
- Project completion rates and adherence to deadlines (target: 90%+)
- Response times to client and team communications (target: <4 hours during work hours)
- Client satisfaction scores (target: >85% satisfaction)
- Team velocity metrics (story points completed per sprint)
- Quality metrics (code review pass rates, document revision cycles)
To track these metrics effectively, organizations should leverage enterprise-grade project management tools such as:
- Asana or Monday.com for general project tracking and team collaboration
- Jira for software development teams
- ClickUp for marketing and creative teams
- Microsoft Project for complex, enterprise-wide initiatives
To support employee wellbeing while maintaining productivity, businesses should establish:
- Regular 1:1 check-ins (weekly minimum)
- Team health surveys (monthly)
- Clear escalation paths for workload concerns
- Performance review cycles adapted for remote work (quarterly)
Addressing Equipment and Technology Challenges
Remote work often comes with equipment challenges, especially when employees use personal devices that may not be secure.
Using Mobile Device Management (MDM) solutions ensures all devices accessing company data are protected. This approach helps safeguard sensitive information while giving employees the flexibility they need.
It’s also important for companies to provide guidelines on personal device use to reduce security risks linked to unmonitored access to company data.
Offering tech support can ease frustrations from connectivity problems or equipment breakdowns.
Streamlining Processes for Effective Remote Work
Optimizing processes in remote work means creating efficient workflows that fit virtual collaboration tools.
Companies should focus on workflow efficiency by cutting unnecessary steps in processes while staying compliant with established guidelines.
Regularly checking existing processes and gathering feedback from team members can strengthen operational resilience.
Encouraging innovation allows teams to suggest improvements based on their daily experiences while working remotely.
Data Management and Compliance in a Remote Context
Data management compliance is crucial as more organizations adopt flexible working setups.
Secure information storage protocols are needed to protect sensitive data and maintain regulatory compliance across different regions where remote workers operate.
Secure Information Storage and Data Transfer Protocols
Using secure data transfer methods like encryption strategies greatly enhances protection during data transmission between users’ devices and central databases.
Virtual Private Networks (VPNs) further shield against unauthorized access when sharing vital information over public networks.
It’s essential to train staff on these protocols so they understand how important proper practices are in preventing breaches or leaks of confidential material during remote operations.
Ensuring Document Security in Remote Workflows
Implementing document security best practices is key for protecting files shared among remote teams, especially those using cloud solutions that require careful monitoring of access rights.
By using file-sharing security measures, only authorized personnel can access sensitive documents.
Cloud security solutions add more layers of protection against cyber threats targeting online-stored documents.
Establishing Robust Backup and Recovery Systems
Creating backup plans specifically for remote teams is necessary; disaster recovery plans must consider both physical loss scenarios and cyber incidents affecting system integrity.
Having a detailed incident response plan enables rapid containment efforts, reducing downtime that could disrupt overall business continuity during crisis situations.
Maintaining Compliance and Protecting Data Privacy
Maintaining regulatory compliance is vital even in telecommuting environments—companies should review employee privacy policies regularly to align with current laws regarding worker protections.
A risk assessment framework helps leaders find vulnerabilities early, addressing gaps before they develop into bigger problems that could threaten organizational stability as businesses shift toward hybrid models mixing office-based roles with fully remote jobs.

HR and Personnel Risks in Remote Work Environments
As companies shift to remote work, they encounter specific HR and personnel risks that need careful management.
Key issues include effective employee management in remote settings, ensuring human resources compliance, addressing psychological risks related to isolation, and promoting employee wellbeing.
Effective Employee Management in Virtual Settings
Managing a remote workforce requires fresh strategies for productivity and engagement.
To monitor performance for remote teams, companies can use digital tools that keep track of progress without being too controlling.
Finding this balance is vital for building trust while keeping accountability high.
Crisis communication is key when unexpected events happen in the organization. Clear channels for sharing information help reduce confusion among team members.
Embracing digital transformation through collaborative platforms can improve communication and boost overall team productivity.
Investing in training programs helps managers develop skills needed for leading virtually.
Creating a culture where feedback is welcomed encourages continuous improvement among employees.
HR and Personnel Risk Metrics and Strategies
Remote Team Retention Strategies:
- Competitive compensation packages with remote work stipends
- Clear career progression paths
- Virtual team building activities
- Professional development opportunities
- Flexible scheduling options
Burnout Prevention Metrics:
- Weekly working hours (alert if >45 hours consistently)
- PTO utilization rates (target: >80% of allocated time)
- After-hours communication frequency
- Project overallocation warnings
- Regular wellbeing surveys
Remote Hiring Best Practices:
- Structured virtual interviews with standardized scoring
- Technical assessment platforms for skills verification
- Virtual culture fit evaluations
- Remote work readiness assessments
- Digital onboarding process with clear milestones
Navigating Compliance Issues Related to Remote Work
Remote work compliance introduces challenges with organizational risk management and adhering to data protection regulations.
Companies should create clear remote work policies outlining expectations about confidentiality, cybersecurity practices, and legal duties under labor laws.
Regular audits are essential for checking compliance with these policies. By spotting gaps early, businesses can take action before small issues grow into bigger ones.
Keeping up with changing regulations—like GDPR or CCPA—is crucial since failing to comply can lead to heavy fines or harm to a company’s reputation.
Communication Challenges in Remote Work
Effective communication requires structured protocols:
- Core Communication Standards:
- “24-hour response rule” for emails during business days
- “Core collaboration hours” (typically 4-hour overlap across time zones)
- Designated “deep work” periods with minimal interruptions
- Emergency escalation procedures for urgent matters
- Virtual Meeting Guidelines:
- Standard meeting durations: 25 minutes (quick sync) or 50 minutes (deep dive)
- Maximum of 3 hours of video meetings per day per employee
- Required pre-meeting agendas and post-meeting action items
- “Camera-on” policy for team meetings to enhance engagement
- Communication Effectiveness Metrics:
- Meeting attendance rates (target: >90%)
- Action item completion rates (target: >85%)
- Employee satisfaction with communication tools (quarterly survey)
- Response time compliance (target: >95% within 24 hours)
Fostering Effective Internal and External Communication
Using secure collaboration tools boosts teamwork while protecting against cyber threats like phishing attacks—an issue many organizations face today.
Training staff on phishing awareness gives them the knowledge to spot suspicious activities online, which helps keep the company safe from cyber threats.
In addition to technical measures like using encryption methods in emails, regular cybersecurity training fosters an ongoing culture of awareness among employees about their online behaviors both at home and work!
Implementing a Proactive Risk Management Framework
Implementing Effective Risk Mitigation Strategies
To manage risks in remote work, companies need strong risk mitigation strategies for telecommuting. First, they should provide cybersecurity training to help employees spot threats and act wisely. Next, incident response planning is essential. It prepares teams to respond quickly if there’s a security breach.
Secure remote access is key to keeping sensitive data safe while allowing employee flexibility. Organizations can enhance security by using tools like virtual private networks (VPNs) and multi-factor authentication (MFA). Moreover, promoting employee cyber hygiene with regular updates on digital security best practices can lower the chance of data breaches.
Deploying Robust Security Measures and Technology Solutions
It’s vital for businesses to use advanced technology solutions to protect their assets against threats.
Endpoint protection software monitors devices used by remote workers, ensuring they meet security standards before accessing corporate networks.
Mobile device management (MDM) tools help IT teams secure smartphones and tablets, stopping unauthorized access.
Cloud security solutions are also important as more companies move online. A zero-trust security model can reduce risks from external attacks by confirming every user’s identity regardless of their location within the network.
VPN security is crucial for encrypting internet connections during remote work sessions. MFA adds another verification layer that strengthens defenses against ransomware attacks.
Developing and Enforcing Clear Security Policies
Having clear remote work policies is essential for good information security management in organizations. These policies should outline what’s expected about communication security in remote settings, including guidelines on handling sensitive information when using collaboration tools or sharing files.
Organizational risk management requires ongoing assessment and updates of these policies based on new threats or changes in operations. Regular reviews help ensure compliance with industry regulations while encouraging accountability among team members who work remotely.
Investing in Comprehensive Training Programs
Investing in solid employee training programs raises awareness about cybersecurity threats faced by remote teams today.
Phishing awareness training teaches staff how to identify fraudulent emails designed to harm company systems or steal personal info.
Also, providing resources about secure collaboration tools helps employees use platforms safely without risking data integrity during teamwork online.
Fostering an environment where cybersecurity becomes a part of daily activities protects organizational assets and promotes overall wellbeing among staff navigating challenges of working from home.
Business Insurance and Risk Transfer
Business insurance plays a critical role in comprehensive risk management for remote workforces.
Organizations should review and update their cyber liability insurance to specifically cover incidents involving remote workers, including data breaches, ransomware attacks, and business interruption losses.
Professional liability and errors & omissions (E&O) coverage should be evaluated to ensure protection extends to work performed from home offices.
Additionally, companies should consider requiring remote employees to verify their home insurance policies adequately cover business equipment and liability for work-related incidents in their homes.
Creating Comprehensive Security Policies
A good risk assessment framework supports the development of thorough security policies that protect digital assets across different departments—especially for those working remotely where traditional oversight may be limited.
This framework should include clear backup and recovery plans tailored for disaster recovery situations affecting teams operating outside regular office spaces.
Such proactive steps ensure business continuity even during unexpected issues like technical failures or natural disasters impacting connectivity options provided by cloud services widely used during telecommuting times.
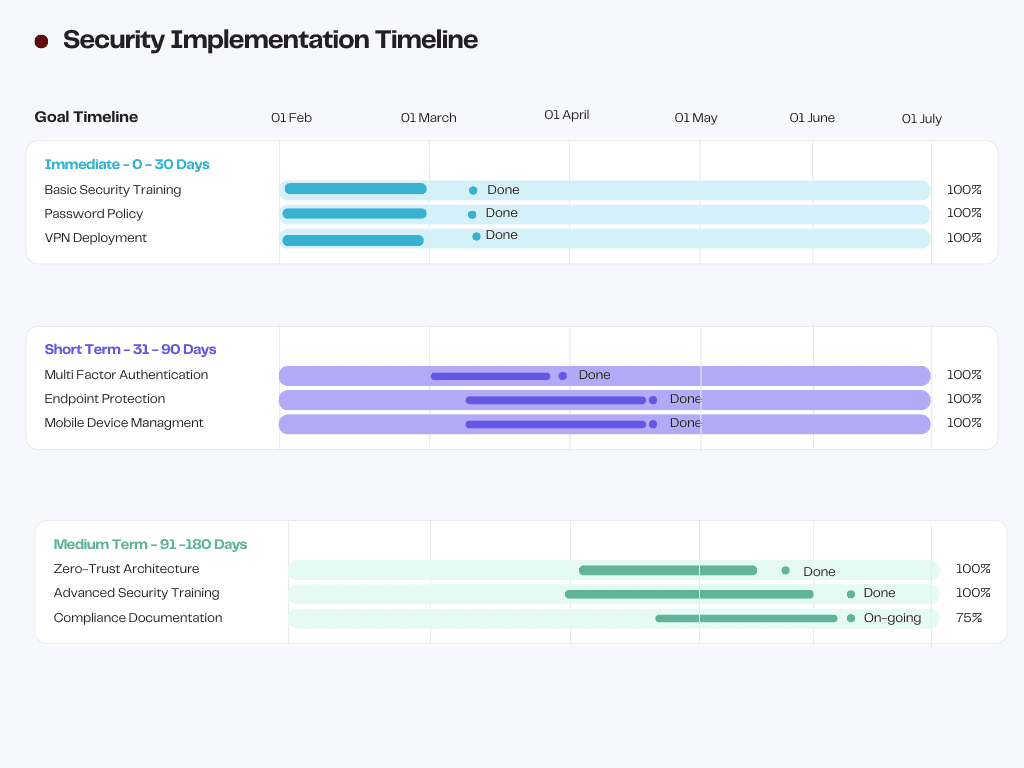
Security Measure Implementation Timeline:
- Immediate (0-30 days):
- Basic security training
- Password policy enforcement
- VPN deployment
- Short-term (31-90 days):
- Multi-factor authentication
- Endpoint protection
- Mobile device management
- Medium-term (91-180 days):
- Zero-trust architecture
- Advanced security training
- Compliance documentation
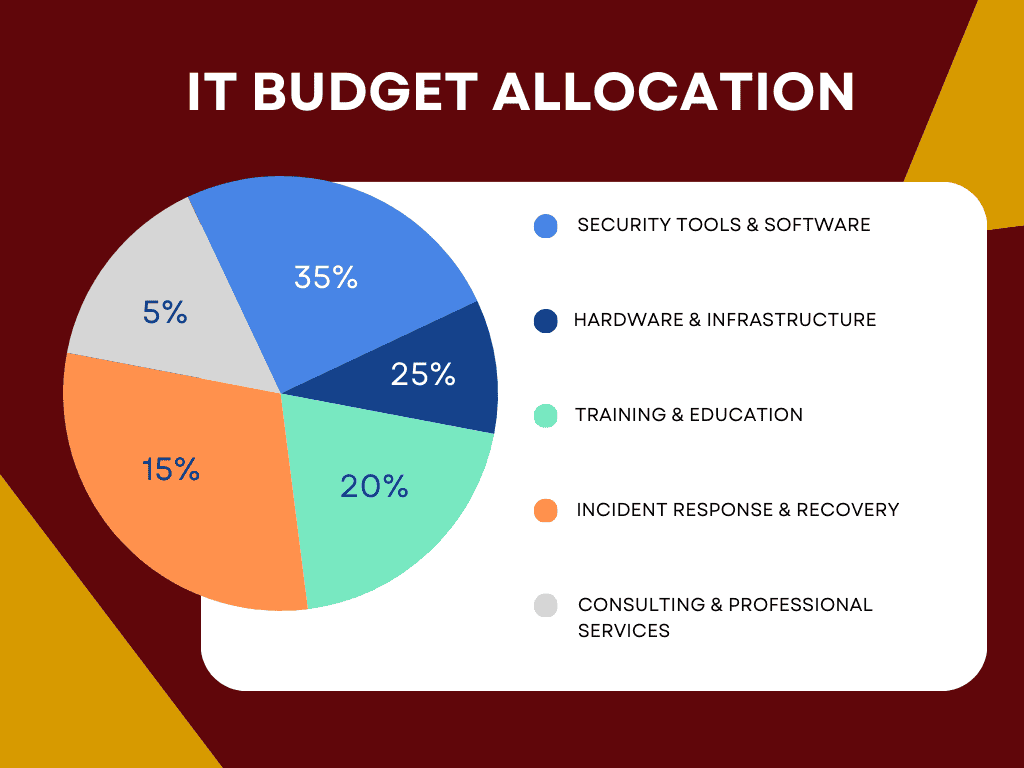
Budget Allocation Guide:
- Security Tools and Software: 35% of IT budget
- Training and Education: 20%
- Hardware and Infrastructure: 25%
- Incident Response and Recovery: 15%
- Consulting and Professional Services: 5%
Developing Effective Training Programs
Training programs must address not only technical aspects related to managing cybersecurity threats but also psychological risks linked with keeping productivity levels up under potentially isolating circumstances often seen in modern workplaces driven by technology reliance—like family-friendly policies that encourage healthy boundaries between work responsibilities and personal commitments shown in daily routines among colleagues working together despite being far apart.
Protecting Your Remote Workforce With The Right Partner
As organizations adapt to remote work environments, implementing comprehensive risk management strategies is crucial.
While the frameworks and security protocols outlined in this document provide a strong foundation, proper business insurance coverage serves as a vital safety net against unforeseen risks.
The Allen Thomas Group understands that each organization’s risk profile is unique and requires a customized approach combining both technological solutions and appropriate insurance coverage.
Remember, risk management in remote work environments is an evolving process that requires regular assessment and adaptation.
By partnering with experienced insurance professionals who understand both traditional and emerging risks, organizations can maintain effective protection while preserving the benefits of remote work.
Contact The Allen Thomas Group to learn how we can help secure your remote workforce through comprehensive insurance solutions and risk management strategies.
Get Precise Risk Management Solutions and Insurance Coverage For Your Business In Minutes
It Just Takes A Few Clicks
Frequently Asked Questions
What is remote work compliance?
Remote work compliance refers to ensuring that remote employees adhere to laws and company policies. Organizations need to create guidelines that outline acceptable practices.
How can organizations monitor performance for remote teams?
Organizations can use performance metrics to track output and engagement. Regular check-ins and feedback sessions help maintain accountability.
What are disaster recovery plans for remote teams?
Disaster recovery plans outline steps to take during unexpected incidents. These plans ensure business continuity and protect vital data.
Why are employee training programs important in remote work?
Employee training programs enhance knowledge about cybersecurity threats. Training helps staff recognize risks and respond effectively.
What is security awareness for remote workers?
Security awareness refers to educating employees on cyber threats. Training improves their ability to recognize phishing attempts or suspicious activities.
How can companies provide effective remote IT support?
Companies can offer support through chat tools or help desk software. Clear protocols allow quick responses to technical issues faced by employees.
Resources Used For The Article:
- https://www.microsoft.com/en-us/security/business/zero-trust
- https://www.onelogin.com/learn/what-is-mfa
- https://www.cisco.com/c/en/us/products/security/vpn-endpoint-security-clients/what-is-vpn.html
- https://www.ibm.com/think/topics/mobile-device-management
- https://www.fortinet.com/resources/cyberglossary/what-is-endpoint-security
- https://www.digitalguardian.com/blog/5-most-secure-collaboration-tools
- https://www.helixstorm.com/blog/security-tips-for-working-remotely
- https://www.rmmagazine.com/articles/article/2024/05/30/navigating-the-legal-risks-of-a-remote-workforce